Protect Your Organization with Security Awareness Training
Security-aware employees are one of the primary lines of defense against cyberattacks in the business world. We know that almost 90% of data breaches are caused by human error*; the human factor is often the weakest link. Security awareness in employees helps mitigate the risk of security breaches and is key to protecting your organization and your customers.
Who is Security Awareness Training (SAT) for?
Security Awareness Training is targeted for employees at all levels, which may include customer service, payroll administration, data entry, and IT staff, as well as other groups connected to your organization, such as board members and volunteer staff.
Why is Security Awareness Training Important?
Security Awareness Training provides your business and employees with knowledge on how best to mitigate risks presented through internet use. This training helps individuals understand their role in facing potential security breaches. Your stance changes from reactive to proactive. Cyber threats will never be eliminated. You can help create an environment that is resilient against threats and has increased its toolbox of capabilities to face threats and mitigate risk.
How effective is SAT?
“Verizon’s 2020 Data Breach Investigation Report, which highlights insights from nearly 4.000 data breaches, found that 67% were caused by an attack targeting people – including credential theft and phishing- and 22% involved human error.”*
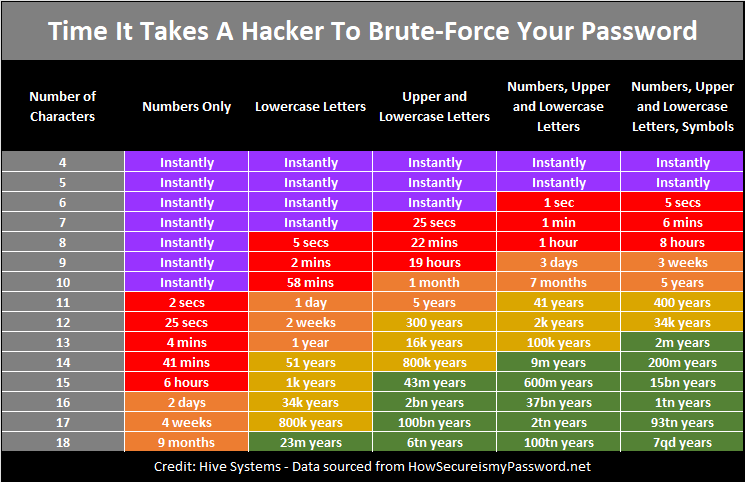
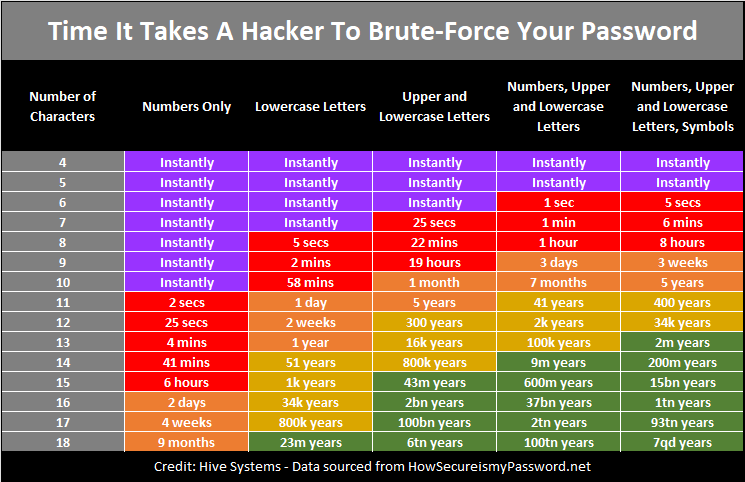
Think about password protection. We all have created passwords in which the organization/company tells you if your password is weak or strong and often provides you with feedback as to what the minimal requirements are to create a strong password on their site. Security Awareness Training assists your employees in being aware of what it takes to truly create a strong password.
We all have various devices that we use daily. It is always intriguing to look up your email address and see if it has been part of a breach. One email typically is connected to multiple devices. It only takes one email breach to threaten all devices. This makes checking your work email on your devices and vice versa a risk. It is good practice to create Security Awareness regulations within your organization. It is also very interesting to look up your email to see if it has been breached.
Consistency in training employees can lessen cybercrimes and their impacts by 40% – 50%.*
What topics does Security Awareness Training cover?
Lessons are 20 – 30 minutes, online, training modules. These lessons teach best cybersecurity practices in a number of topics. These include:
- Phishing – The lesson defines phishing (a form of fraud in which an attacker masquerades as a reputable entity or person in email or other forms of communication), how to identify it, and what to do if phishing is suspected. Users are given several examples of phishing emails.
- Password Control – Users are taught the importance of proper passwords and how to construct them. Users are given examples of strong and weak passwords and will then practice constructing stronger, unique passwords.
- Password Creation – Users are taught the importance of proper passwords and how to construct them. Users are given examples of strong and weak passwords and will practice constructing passwords that are unique to each site.
- Password/Multi-Factor Authentication (MFS) – The lesson covers MFA and password managers. It goes over why MFA is important and the best practices for using it to add an extra level of security to your accounts. The lesson also aids account holders in understanding the dangers posed by writing down passwords, saving passwords in browsers and accounts, and learning the risks and benefits of using password managers.
- Social Media – Users learn best practices to keep themselves safe on social media, using strong security settings and thoughtful consideration of what they share about themselves and their organizations.
- Developing your SecurityPosture
- Malware and Ransomware – The lesson defines malware (malicious software) and ransomware (the type of malware that blocks access to devices and or data, often until payment to remove it is made), then describes what attacks can look like, prevention methods, and what impacts malware can have on an organization.
- Remote Work
- Work from Home – The lesson focuses on securing the home workspace, devices, and network. Users learn the dangers of unknown networks, the importance of securing devices in transit and public places, and how to handle
secure information in public places both on devices and in calls. - Mobile Device – This lesson covers foundational information to keep data safe on and when using a mobile device,
including app permissions, phone calls, network and Bluetooth connection in public areas, what it means to share information on your mobile devices, and exactly what information you are sharing with those apps. - Device – This lesson covers how to safely navigate the use of personal devices such as smartphones, tablets, and smartwatches since portability increases the risk of devices being lost or stolen as well as all the data they hold. This lesson also covers how to safely use a USB, what data is safe for storing on a USB device, and the safeguards for securing data on a USB device.
- Work from Home – The lesson focuses on securing the home workspace, devices, and network. Users learn the dangers of unknown networks, the importance of securing devices in transit and public places, and how to handle
- Social Engineering – Fraudsters will seek to raise emotions such as urgency or fear, in the hope that employees will disclose sensitive information or access a malicious attachment. This lesson covers why social engineering methods are so effective, how to identify threat actors, and how to avoid common social engineering scams and light tailgating.
- Surfing the Web
- Browser Safety – This lesson covers how to stay safe on the internet by avoiding risky behavior and common traps; recognizing unsafe URLs, common components, and potential risks within a website, and how to apply practices that will make browsing the internet safer.
- 5 Minute Collection – This lesson covers three topics in one assignment. It will go over fraud and compliance and why security protocols should be followed. This lesson also covers the different types of browser cookies websites use to track and store data about users, and aid in understanding better ways to control user privacy and security when browsing online.
- Data Protection
- Personal Identifiable Information (PII) – The lesson covers the topic of PII and the security precautions organizations should take when handling other people’s personal information.
What are the benefits of Security Awareness Training?
Security awareness training is asynchronous and offered at a low cost. You may contact a team member to set up your team. The cost will reduce by 50% from July 1st, 2024 – December 31st, 2024 to a one-time ᶧ$15 flat enrollment fee per trainee for the remainder of the 2024 calendar year (ᶧPrivate sector pricing). Our team works with your team to encourage employees to finish the training.
The CyberMontana Team provides detailed monthly reports. As an organization, you will be able to note the percentage of training completers, assessment scores, and so much more.
There is also available live in-person or virtual training that is customizable to meet the individual needs of each organization. To schedule a live training, please contact info@cybyermontana.org.
Some organizations look for employees to have a badge or certificate to accompany their training. CyberMontana’s Security Awareness program offers badging and a certificate of completion for training completers.
- The Security Awareness Individual Proficiency Badge will be available to individual users of an organization who complete at least 75% of their assigned Security Awareness Training (SAT) modules.
- The Security Awareness Business Proficiency Badge is available to organizations whose users complete at least 75% of their assigned Security Awareness Training (SAT) modules.
How to Get Started with the Security Awareness Program?
Getting started is quite easy. The CyberMontana website has a Security Awareness Training page in which you can get more information and complete an interest form. Someone from our team will reach out to you. You can also contact Matt (matt.collins@mso.umt.edu) directly to get you and your organization started.
We also offer a demo lesson so that you have an opportunity to see what a lesson looks like. Lessons vary each month. You can reach out to a team member through the contact form found here to register. Lessons scheduled for the year include:
June: Security 101
July: Work from Home
August: Cyber Hygiene Essentials
September: Phishing Essentials
October: Malware & Ransomware
November: Passwords and Multi-Factor Authentication (MFA)
December: Social Engineering Basics
Conclusion
There is no question we are all at risk for cyber threats via cyberattacks and data breaches. The number of attacks each year increases significantly and these attacks continue to become more sophisticated. The best and most successful pathway to protecting yourself and your organization is to educate and prepare yourself and your team. Please contact us if you are interested in our Security Awareness Training, or our other Cybersecurity Training options that are available (K-12 education, Cyber Rapid Training Certification of Technical Studies Program, Workforce Development/Upskilling).


















![Everything You Need to Know About CyberMT’s GenCyber Camps [2023]](https://news.cyber.windfall.tools/wp-content/uploads/2024/04/CyberMT-blog-CTA-and-images-14.png.webp)

![Why Is Security Awareness Training Important? [2023]](https://news.cyber.windfall.tools/wp-content/uploads/2024/04/CyberMT-blog-CTA-and-images-13.png.webp)